Cloudflare Quad-1 DNS

This year I have witnessed too many DNS stories - rising from the Government censorship programs to privacy-centric secure DNS (DNS over TLS) in order to protect the customers’ queries from profiling or profiting businesses. There are some DNS which are attempting to block the malicious sites (IBM Quad9 DNS and SafeDNS) while others are trying to give un-restricted access to the world (Google DNS and CISCO OpenDNS) at low or no costs.
Yesterday, I read that Cloudflare has joined the race with it’s DNS service (Quad1, or 1.1.1.1), and before I dig further (#punintended) let me tell you - it’s blazing fast! Initially I thought it’s a classic April Fool’s prank but then Quad1, or 1.1.1.1 or 4/1 made sense. This is not a prank, and it works just as proposed. Now, this blog post shall summarize some speed tests, and highlight why it’s best to use Cloudflare Quad1 DNS.
Quad1 DNS 1.1.1.1 Speed Test
To test the query time speeds (in milliseconds or ms), I shall resolve 3 sites: cybersins.com, my friend’s website palunite.de and blog namastehappiness.com against 4 existing DNS services - Google DNS (8.8.8.8), OpenDNS (208.67.222.222), SafeDNS (195.46.39.39), IBM Quad9 DNS (9.9.9.9) and Cloudflare Quad1 (1.1.1.1)
| Websites/DNS | Google DNS | Open DNS | IBM Quad9 | Safe DNS | CloudFlare |
|---|---|---|---|---|---|
| cybersins.com | 158 | 187 | 43 | 238 | 6 |
| palunite.de | 365 | 476 | 233 | 338 | 3 |
| namastehappiness.com | 207 | 231 | 178 | 336 | 3 |
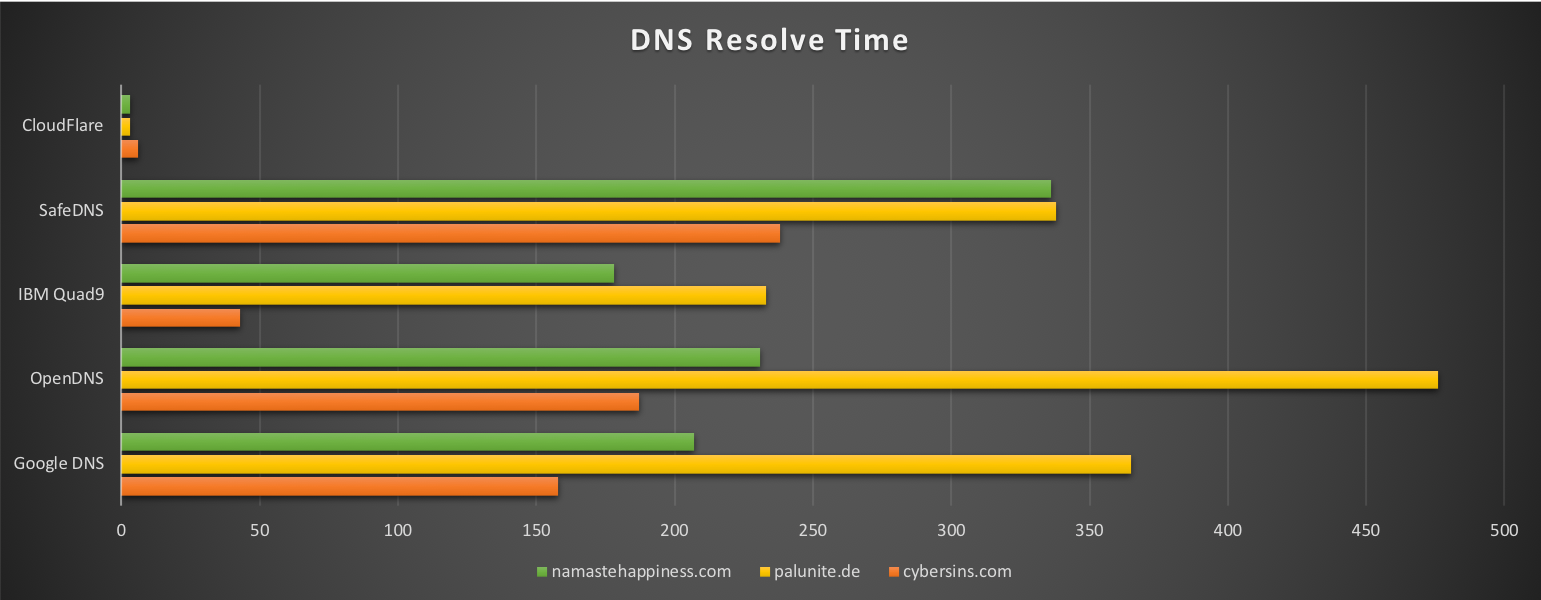
This looks so unrealistic, that I had to execute these tests again to verify, and these numbers are indeed true.
Privacy and Security with Quad1 DNS 1.1.1.1
This is the key element that has not been addressed for quite a while. The existing DNS services are slow, but as well store logs and can profile a user based on the domains they query. The existing DNS services run on UDP port 53, and are vulnerable to MITM (man in the middle) kind of attacks. Also, your ISP has visibility in this clear text traffic to sensor or monetize you, if required. In the blogpost last weekend, Matthew Prince, co-founder and CEO of Cloudflare mentioned,
The web should have been encrypted from the beginning. It’s a bug it wasn’t. We’re doing what we can do fix it … DNS itself is a 35-year-old protocol and it’s showing its age. It was never designed with privacy or security in mind.
The Cloudflare Quad1 DNS overcomes this by supporting both DNS over TLS and HTTPS which means you can setup your internal DNS server and then route the queries to Cloudflare DNS over TLS or HTTPS. To address the story behind the Quad1 or 1.1.1.1 choice, Matthew Prince quoted,
But DNS resolvers inherently can’t use a catchy domain because they are what have to be queried in order to figure out the IP address of a domain. It’s a chicken and egg problem. And, if we wanted the service to be of help in times of crisis like the attempted Turkish coup, we needed something easy enough to remember and spraypaint on walls.
Kudos to Cloudflare for launching this service, and committing to the privacy and security of the end-users in keeping short-lived logs. Cloudflare confirmed that they don’t see a need to write customer’s IP addresses to the disk, and retain the logs for more than 24 hours.
Cheers and be safe.
