CertDB is a Free SSL certificate Search Engine and Analysis Platform

How many times have you stumbled on the SSL certificate, and the only things that you cared about were Common Name (CN), DNS Names, Dates (issue and expiry)? Do you know SSL certificate can speak so much about you/ your firm? It can tell stories and motives; you can gather a good intelligence from them - which companies are hosting new domains, sub-domains; did they just revoke the last certificate? Or, why some firm switched its vendors/ CA(s)? We all have read that SSL certificates have always been the talk of the town for their inherent strength but weak issuance process, i.e. the chain of command relying on the Certificate Authorities, (aka the business firms) but haven’t played with them in real-time. There are search engines available but none of them as comprehensive, fast and free as CertDB
There have been quite a few attacks and hacks where Certificate Authorities were targeted1 by hacking groups2 or even involved3 directly. Even though the vast initiatives by browsers and firms to regularly monitor SSL certificates4, improve browser behaviours for awareness5 and revoke the bad ones has been highly appreciated, the pentesters often don’t find much during the comprehensive assessment. Recently, there has been an uproar on the business interests of CA(s) with the issuance, so much so that some are being tagged as bad and untrusted CA6 for not doing job well. Companies are moving aggressively to HTTPS especially with the recent introduction of LetsEncrypt Wildcard Certificates. But we haven’t seen the use of all this information on a common platform to further analyse the certificates and assess their digital SSL footprint and gather valuable intelligence.
This is where CertDB steps in. A great project maintained by smart people and FREE forever7 for the public. I spent last few weeks accessing their services, and the platform and my short verdict says - It is great! It does have some quirks, but highly recommended!
The crt.sh and CertDB serve different objectives. while crt.sh gets the data from certificate transparency (CT) logging system where “legit” CA submit the certs in “real time”; CertDB is based on the scanning the IPv4 segment, domains and “finding & analyzing” certificates - good or bad.
CertDB can also find self-signed certificates, which crt.sh can not. Hence, CertDB can give a realistic view of HTTPS - which IP is using what certs, self-signed, invalid CA etc; while crt.sh shows the “good” law-abiding view, per say.
What is CertDB?
CertDB is an Internet search engine for SSL certificates. In simple terms, it parses the certificate and then makes different fields indexable for the user to execute search queries. It indexes the following common information,
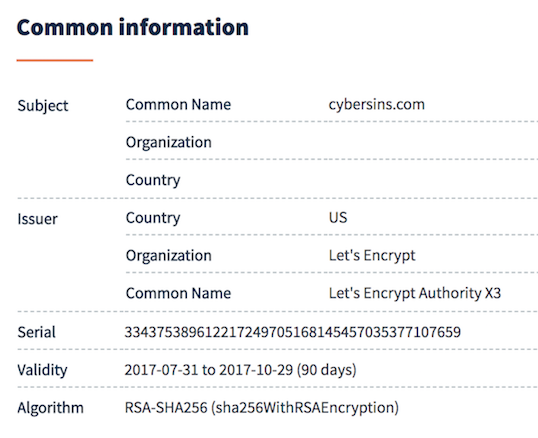
| Field | Details |
|---|---|
| Subject | Country, State, Category, Serial Number, Locality, Organization, Common Name |
| Issuer | Country, State, Locality, Organization, Common Name |
| Others | Public Key IP Address related to the domain, Validity Dates |
| Fingerprint | SHA1, SHA256 and MD5 |
| Extensions | Usage, Subject Key ID, Authority Key ID, ALT Names, Certificate Policies |
Now once you have extracted these fields, you can query and generate intelligence around it. You have these fields available with a logical query, and can be clubbed together to make complex queries. CertDB also provides raw certificates, public key and json formatted certificate information available for download. Recently they have integrated Alexa Ranking with the domains/ IP addresses and all of this information has been filtered and is available as lists - top domains, top organizations, top countries, top issuers etc.
One such exciting list is “expiring certificates” where you can find the list of Domains/ Organizations whose certificates are about to expire. This kind of information can be convenient while auditing or assessing the firm’s digital footprint.
Real-time updates
While the documentation says the CertDB continuously scans every reachable web-server, on the Internet; the lab tests are not conclusive. I have asked the team to clarify and shall publish the response as part of the interview once I have a confirmed reply. But, it’s appreciable that once their scanner detects the certificate, the information is available for the public to perform the required analysis in near real-time.
Use Cases
While we have all the information extracted from the digital certificates, we have to filter the results to get the required information via GUI or API. The GUI is open to all and can be used to do such queries with search-box, but to use the API one has to register an account.
You can register at https://certdb.com/signup, and an API key shall be allotted to you to perform 1000 queries a day with maximum 1000 results per query.
| Field | Value |
|---|---|
| URL | https://certdb.net/api |
| Method | GET, POST |
| api_key | |
| q | Any query (just like in search interface) |
| response_type | 0 — JSON list of the dictionary with found certificates with all details 1 — JSON list of found certificates in base64 2 — JSON list of distinct organizations from found certificates 3 — JSON list of distinct domains from found certificates |
It takes 30 seconds to register and receive the API Key. Here are few examples of querying the right information,
- Search for Issuer “Godaddy” issued certificate for an “Italian region” domain/company.
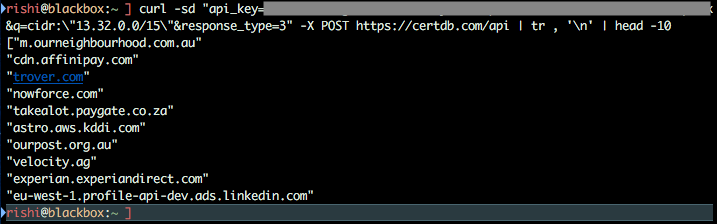
issuer:"Godaddy.com" country:"Italy" - Certificates issued to a subnet or IP range (example: Amazon Global IP Range: 13.32.0.0/158
cidr:"13.32.0.0/15"(example: replace,with newline and only list first 10 resultstr , '\n' | head -10
- Expiring in next ten days.
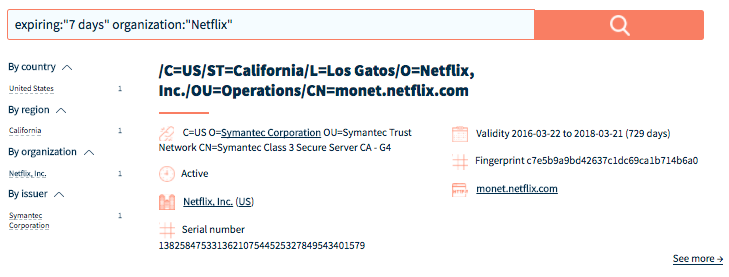
expiring:"10 days" - Expiring certificates in next seven days for Netflix organization
expiring:"7 days" organization:"Netflix"
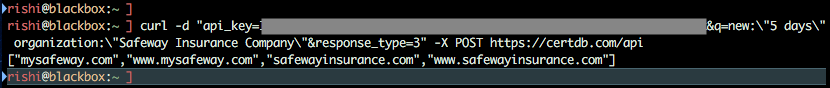
- New Certificates in last five days for Safeway Insurance Company (via API)
new:"5 days" organization:"Safeway Insurance Company"
There can be many such cases where you would like to know the certificates issued to a firm in the past; or if the firm recently got a new domain/ sub-domain and looking for a new business line. I could think of the following interesting cases if I am doing an assessment,
- Dork all the subdomains;
site:example.comand then start negating in a loop as per the first result.site:example.com -wwwtosite:example.com -www -test. Or, use a threat intel tool to gather the sub-domains and validate if they all have SSL certificates. Manually check, and report if some domains are not on HTTPS (Refer: Google will be hard on you if you are not on HTTPS!) - If you are technically assessing a company, do check their domains names and Organization.
q="organization:"Example Inc."and you will be surprised to see sometimes firms are not aware of the domains on their name, or certificate issued by them but not renewed on time.
Quirks
While the service is great, there are few issues as well which the team is working on,
- The errors are not customized. If the API queries are wrong; it dumps a lot of debug data which must be removed.
- The API key cannot be re-generated or revoked. You may have to contact CertDB support to revoke it.
- The API Key can be used in a
GETrequest. It is not recommended as it can be cached at many hops (example: proxy) - The documentation is not comprehensive, and probably more detailed information is needed when using API calls.
- The site doesn’t provide an example of API interaction. In my opinion, CertDB should write a page with few examples using Python, CURL, Ruby, Perl and other common languages including
jsonparsing of the results.
Conclusion
It’s been few weeks since I am using this service, and my frank opinion is it has great potential and use. I am using this service while assessing AWS instances, and Fortune 500 firms. I have also found some expiring certificates for the clients and informed them in due course of time. I would highly recommend you to have a look and register an account. You can also set a cron job to check the dates/ digital SSL footprint of an organization.
Next Steps: I shall soon be publishing an interview with their team asking for more details on the roadmap, competition, and improvements.
Cover Image Credit: Photo by Rubén Bagüés
https://arstechnica.com/information-technology/2011/03/independent-iranian-hacker-claims-responsibility-for-comodo-hack/?source=cybersins ↩︎
https://arstechnica.com/information-technology/2011/08/earlier-this-year-an-iranian/?source=cybersins ↩︎
https://arstechnica.com/information-technology/2018/03/23000-https-certificates-axed-after-ceo-e-mails-private-keys/?source=cybersins ↩︎
https://security.googleblog.com/2018/02/a-secure-web-is-here-to-stay.html?source=cybersins ↩︎
https://security.googleblog.com/2018/03/distrust-of-symantec-pki-immediate.html?source=cybersins ↩︎
https://cybersins.com/spyse-exclusive-interview-with-cybersins-free-security-tools/, CERTDB confirms this “project” will always be free to use. ↩︎
