Don't aid spammers with LinkedIN Open Network. LION or Sheep

It’s 21st century, the year 2014 and we are still on ground zero talking about spam emails and attacks like spear phishing. No matter how stringent your controls are, how much you have invest in your “defense in depth” approach, a single human being of your firm clicking a link on an unsolicited email can crumble your empire. This is not at all melodramatic as it sounds. It is for real, is scary and sad. I with this blog post, would wish to take you to one of the easiest way to harvest email addresses.
Once an attacker has these addresses, they can be used for targeted attacks, targeted spams or even hell yeah, just spams! You may feel why am I sharing this way of email harvesting, but lets say, this is my way to tell you – Grow up, and don’t be so naive online. Also, if you are publishing your mail address online in the dumbest easiest of ways, I’m sure you will click the links as well. Let’s see how its done in the least time.
Problem Statement –
Gather corporate email addresses for middle management people working with some lead/ big companies.
Solution 1 – Dirty way! (if you know the person name)
One of the quickest ways, is to find out the email syntax for a firm, and then align it with the name of the employee that you know. Example – If the firm uses the template – [email protected] then I believe you know what can be the probable email address for an employee whose name you are aware of.
But, then you’ll have to guess the kind of emails he/she usually gets and the email content that can lure him/ her to click. A little tricky job, and would need some social engineering or profiling skills.
Know the Employee Name → Guess the Email ID → Guess the Subject → Mail & Target
Solution 2 – Search & Target (much more efficient)
In this solution the idea is to find people of a particular firm whose addresses you can grab, and then make sure they will open your email with a subject you are sure they are looking forward to.
Search the Email ID → Understand the context → Interested in this person? → Mail & Target
Now, when it comes to search, I have seen people are more so lost. They don’t know how and what to search in a targeted manner etc. so, here is an easy way out with the help of LinkedIn Groups. These groups though highly recommended to be a part of, for all good reasons, also attract email id harvesters. These attackers lurk in these groups, right in plain sight and harvest legit mail addresses with information on the owners.
Let me show you an example on manual and how we can automate it I automated it. I searched for groups related to LION (LinkedIn Open Network) on LinkedIn and specially with posts that talk about “Share your email address, to be a part of LION”. The whole concept of LION, and such headings usually cracks me up! But anyways, lets do this.
First, a search on LinkedIn suggested 513 groups of which, 243 are open groups related to LION. Example –
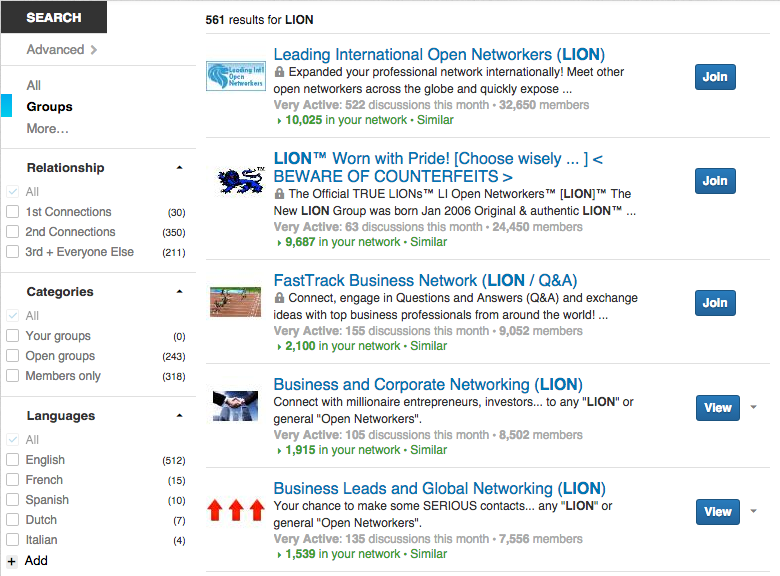
Now, I will show couple of examples for you to witness the sink of email addresses, and very well the context,
- https://www.linkedin.com/groups/2014-Open-Networker-LION-List-4034311.S.5806350438659821569
- https://www.linkedin.com/groups/Black-Belt-POWER-Networkers-4034311
and there are thousands of such groups/ posts. And, the icing on the cake is they are “open” because they are the LION(s).
So, let me know show you how will this work out for a spammer? Time to switch hats. Remember, this is FOR EDUCATIONAL PURPOSES and carry NO INTENTION WHATSOEVER to any wrong means.
Disclaimer: The information sources are public, the names are as stated as listed in the profile, and the content has not been altered for any personal means.
Let’s read this post by Jim here at a LinkedIn group – IT Audit.
This post received a small but considerable 62 comments. And, as per the comments, one could very well figure out no one has received the Checklist. Here are some folks who asked with their email addresses listed in the comments (e.g please share a copy, my address is – [email protected]),
- Professional Accountant, IS Auditor and Certified COBIT 5 Trainer
- IT Manager
- Team Leader – IT Audit at a Financial Firm
- Manager at IT Advisory Services
- Senior Manager (IT Audit and Advisory)
- IT Auditor
- Risk and Compliance Professional
and many others. Though the majority have their personal addresses listed, some have their office email addresses as well. Now, what will an evil minded person do? He/she will make an excel file, or a URL with malicious intend and send a copy to all stating he/she is Jim, the guy they expect in their inbox. If you counter me with this statement – “I will scan, validate and will open it carefully in a sandboxed machine.” , I will chuckle as we all know otherwise. Its gonna be sitting right on their Windows Desktop waiting to do it’s wonders! Game over.
Now when you got the idea, check these statistics (all taken from sharing emails to become a LION type posts)
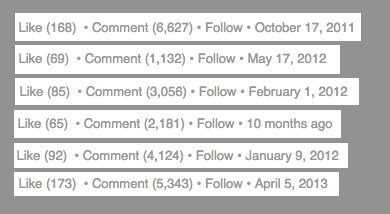
If you seriously believe that your perimeter defence will protect you from a targeted spam, you my friend, can strip your designation and walk off. It’s gonna be a collaborative effort if we could ever protect 100% of the resources from every type of attack. But yes, we can be attentive and cautious. This in our hands. Next time, chose wisely if you really wanna be a lion or a sheep.
Cover Image: Original Photo by Joanna Kosinska
