What should you look for in a Pen-test, anyway?

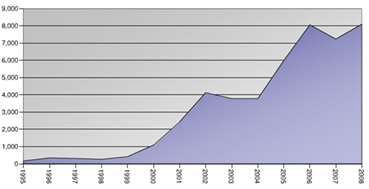
Vulnerabilities are increasing by leaps and bounds and any industry – technical or non-technical has to grow its security in sync or else, it is highly vulnerable and lucrative target. There is news of data loss, breaches every now and then. A rough estimate of the growth of vulnerabilities (as reported) over last decade (1995-2008) is shown in Figure 1. This accounts to vulnerabilities as reported, wherein there are hundreds of active (non-reported or un-patched) vulnerabilities floating underground which are in the hands of money driven and black hat profit driven attackers.
This exponential growth in vulnerabilities and ease in exploitation with automated kits demands the security to be on the tows. Every time the topic of information security is discussed, it has to be related to three of its key pillars – Protection, Detection and Response (Figure 2). These pillars, if strengthened well, can lower the chances of any known vulnerabilities be exploited in your network. To keep the security on its toes and its top notch maintenance, a client has to consider a penetration testing engagement to verify the security controls and validate response timings. So, what is Penetration testing all about?
Penetration Testing (or PT) is a widely used term with a broad meaning. It is generally referred to as a method to evaluate the security posture of a network, system or a device by simulating an attack or hacker’s activity. Though it is very much conjugated with Vulnerability Management (or VM) but there is a difference in their application and implication. While VM is commonly a part of any PT or risk assessment, but on a general note PT has more to do with active exploitation of the resources in scope, where in VM has to deal with the identification and quantification of vulnerabilities but not their exploitation. Overall a PenTest provides assessment support on all these pillars – verifies the security controls to check if they can be bypassed, and verifies the log, monitoring and alerting systems.
We are living in an era where cyber war and cyber-attacks are no more fictional plays. Even cyber espionages are also a part of controversial theories and discussions. We have hundreds of portals with security feeds, malware news and recent vulnerabilities available online. But are all these news, podcasts and blogs important for your business? You have deployed a number of software and devices in your network and you specifically need a risk assessment report thatcan cater to your requirements and technology setup instead of all the white papers shouting of exploitable applications which are not even installed inside your enterprise perimeter. An enterprise PT report usually has three main sections as shown in Figure 3, customized to the enterprise business model.
Each of these sections can be further categorized into sub topics as per application/network setups, security controls, technicalities/processes and compliance terms & conditions etc. On a short note the background information refers to the type of business the client is involved into. The main reason for this is to prioritize the severity ratings and provide remediation methods that can suite his IT and business models. Similarly the discovery phase of the report includes the network architecture, application/host details or physical/virtual address space information and this helps in determining the scope of the Penetration Testing that is to be carry forward. According to the findings of this discovery phase, the vulnerability identification/exploitation and remediation procedures will be attempted.

Following the planning phase, it’s the time to find something and assess it. To document the observations, vulnerability identification is considered to assess the in-scope resources and quantify possible bugs, gaps and vulnerabilities in the applications, software and/or devices. After confirming these findings and observations with various manual methods, tools and automated systems, the phase of vulnerability exploitation or infiltration comes into picture. This phase not only exploits the vulnerabilities but also confirms the impact of exploitation in accordance with the client’s business role and model. The key importance is that the exploitation of vulnerability may not be equally critical to two different business units with different priorities and offerings.
Finally the recommendation phase which includes the mitigation steps to render the vulnerability non-exploitable or even to patch the applications as per the availability of new versions, hotfix and other information. A step further under the recommendation, it can also include implementation of new services, devices or software to prevent the attacks on the client’s network and business enterprise. With all these phases briefed, the common thing about them is – None of these approaches is a standard one, which means, with every client it differs; with every business model, the execution of these phases take a twist, and with every virtual/physical location of the client, there are changes and customizations needed. These are just the headings but the content highly depends on the client. And this makes it a business need, and offering worthy of an investment and understanding.
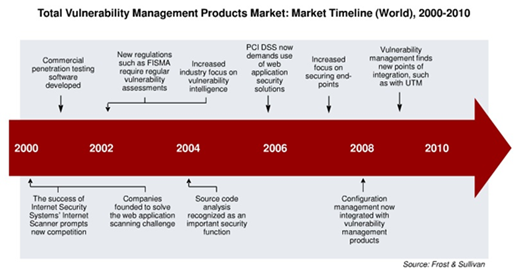
To facilitate a penetration testing, there are various automated vulnerability management solutions available in the market. Vulnerability Management (VM) solutions play in important part in automating the vulnerability assessment phase and documenting reports and graphs for the enterprise. These VM solutions have evolved and are pretty much single clicked operated these days. A brief layout of their market growth is projected in Figure 4. You feed the pre-requisites, and it will generate the final report with all the assessments done! It just is different for the sake that the vulnerability exploitation often will not be a part of it, and the security of the findings in the report will be based on the generic nature of vulnerability rather than on your business model.
The key dependency of a client’s response and approach depends on the understanding of the PT engagement in reference to his business and enterprise network. As per my experience, the clients (mostly businesses) usually have two modes of operations specific to investments in information security services,
- Market Driven
- Privacy Driven
Though there are always grey areas with a bird’s view, but on a granular level there are different key driving factors for a client to be concerned about its investments of funds – the flow towards development or towards its security. Some client may give a higher importance to its consumer base and their information, and some to their final products and services. There is a thin line, but surely it exists!
Market Driven Operations
The market driven approach is mainly regulated with the thought of being a step ahead of competitors, always focused to have all the high level certificates which can entitle their enterprise a top notch place in reference to available compliances, policies and standards. The key reason of such an approach is to acquire a market position and trust of its customers with valid proofs in ink.
To approach this client, the key criteria is – How this ‘pen-testing service’ will give it an edge over others? All the discussions revolve around it, and the presentation slides have the key motto of showing that this PT service is worth of providing them the boost (an advantage or a necessity). Irrespective of the client’s stand in the market, he is ready to opt and invest in sources which can give its customers a better trust and confidence in its product and services. And more importantly he can publicize it too!
In the discussions there are various questions, a client wish to confer about. The questions can range from the proficiencies of the PT team to the incoming challenges, pressure from the market, and security community etc.
Privacy Driven Operations
This is a section of clients which are actually concerned about the security, the network traffic and uptime/downtime of services. These clients invest in security, as they do not wish an attacker to compromise their servers/networks and are very much aware of the key worms, malware and attacks through news, and sometimes even via underground networks. These clients have people appointed to understand ‘technical terms’, findings and people who can cross question a pen-testing team.
To approach this client, the key criteria is – How is this ‘pen-testing service’ different from others? Even when the client is highly literate of its security, and has deployed security guidelines to its different business and development teams, what makes it important for it to invest in a third party penetration testing service. The presentation slides revolve around the technical superiorities of the team, and needs a detailed information intelligence to gather before ringing the bell.
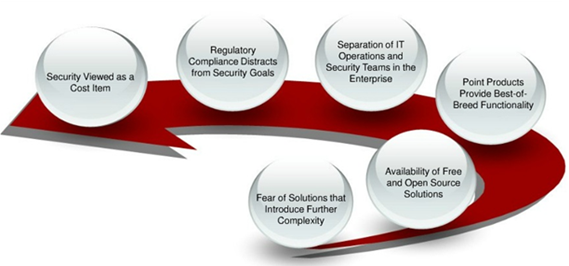
During the kickoff meetings or even the proposal presentation, the pen-testing team occasionally receive ‘curious’ questions from the customer. Most of them point to a fundamental question – How to be sure that your team (PT team) falls in the league of ‘good’ guys? Even though it’s obvious to any information security firm, but can raise an eyebrow if the firm has a one liner approach towards information security in their corporate policy but has no knowledge of it. Even when you are technically sound, you have to prove that the pen-testing will not create any mess at the customer end, and more importantly, how this engagement report in all proportions, will be beneficial for the client. There are legal contracts to be signed and all the important paper work performed, but convincing a ‘non-technical’ client about the benefits of PT is the most challenging part. These days, vulnerability management solutions also face restraints from the industry. Some of such restraints are listed in Figure 5.
I will share one such experience with a client. This client is in health care business but for confidentiality reasons, and scope of this article lets’ not dive into its location and name. Our team scheduled an appointment with the MD of this firm and proposed the need and requirement of a full-fledged PT engagement. Now the foremost step before you walk-in to any customer is to have thorough background knowledge including nature of business, locations, data criticality, online foot print etc. We were not dealing with the compliance checks or audits and were a technical team to propose & perform a PT engagement. To strengthen our proposal, we had already gathered enough information about the cracks in their security observing their flow of work and via different sources. The firm’s MD and some other members with professed ‘security knowledge’ had a raised eyebrow as soon as we presented our synopsis of the complete plan before digging into the in-depth discussions.
The four (4) key questions were,
Question 1. Why do we need a PenTest when we never have been breached in the past and have a good track record in security?
Ans 1. The reason that you have not been breached in the past doesn’t quantify and insure security for the future. There can be other possibilities such as,
- You have been breached but are still unaware of it as the attacker just copied the information, without altering any document. A PT assignment may help you find traces of such a breach.
- You have not been breached because the attackers couldn’t find any golden egg in your basket or are unaware of your worthy existence. With your expansion, and bright business prospects you can be the next target. A PT report will document such holes before anyone else does!
- It may not be an external breach, but internal employee can be trading information with external entities. How will you regulate and verify privilege escalations? A PT report will document gaps in security policies and configurations to the management.
Question 2. We have a secured facility with all kinds of physical and virtual controls, then why do we need this kind of assessment?
Ans 2. Physical and virtual controls are appreciable but how often there are checks that people are following it. Users and employees adhere to these checks and have not devised a way around to bypass them. To deploy and to maintain are two different realms of security, and individuals if not checked and educated/trained on time usually tend to look for short-cuts.
- How do you maintain the ID cards, and to ensure that no duplicate card be issued without proper documentation and deactivation of previous record. PT report will also include if there are any duplicate logs or possible intrusions using the same electronic key
- How do you maintain the permission levels for different individuals in the firm where a certain group is restricted to certain facility? PT report will contain the permission levels and possible breaches if there is a firm policy. And we can also provide guidance in documenting such policy.
Question 3. The customers have access to their records with a password protected online portal, so no one else can get hold of their information.
Ans 3. Password security is much more complex than it is perceived by the firms and there are many such aspects which need to be considered in accordance with passwords,
- How to maintain the complexity of passwords? Does the online portal enforce keeping strong alphanumeric passwords of a minimum permissible length? If they are not met, any weak password is as simple as an open door to break.
PT assignment will assess the security of such controls and permissible passwords and complexities.
- How to make sure the session tokens and/or cookies are random and generated and/or expired in due course of time. If not managed and randomized properly, passwords are of no use as anyone can validate anyone’s session.
A PT report will document all such findings and possible brute-force attacks and randomization of such values
- Even if all the password regulations are met, complexities and randomization of cookies and session is dealt with, there are literally hundreds of checks and vulnerabilities in an ill-coded or obsolete application that can let an attacker breach and steal your resources
*A PT report will present all such findings, application’s vulnerability and will also provide the ways to mitigate them
Question 4. We have an anti-malware solution, firewalls etc. deployed and no-one has the right to tinker with it except a third party security vendor. We are very safe!
Ans 4. Anti-malware solution Firewalls, IDS/IPS are as good as a soldier with shields and ammunitions but everything depends on how he is trained to protect.
- How to configure the firewall to best suite your business needs, and network traffic requirements
PT report helps in analyzing the configuration of the servers, devices (firewall/IDS/IPS or UTM), and clients to the best of hardened security.
- How to make sure that the configurations performed by the administrator are in best results to your business
PT report helps find the gaps against popular guidelines, CIS benchmarks or firm’s global policies
I am sure that these are the kind of questions asked by individuals who are oblivious to security incidents and real world case studies. They hide their resources and confide on the security under the shadows of the past. With due respect, we explained the answers to all such queries focusing on the needs of security assessments. But some customers have a very different set of reasons ‘against’ penetration testing,
R1. We already know where everything is broken.
R2. If you tell us what’s wrong, we’ll have to fix it. R3. We don’t have anything that hackers want. R4. We’re too small to matter. R5. We haven’t fixed the things you found broken last time. R6. Our employees don’t know how to do bad things.
While these reasons seem to be challenging enough to refute by any pen-tester, they are certainly not! Any security team can negate these reasons with proper homework and case studies.
[R1] Knowing that you (customer) are broken doesn’t help you in the knowledge on how to mend the cracks. There are two approaches,
- Band-Aid Approach which means temporary mending of a crack in security
- Hardened Approach which reflects strong solution to fix the gap
A pen-test report can help you with the recommendations and mitigations steps on the gaps that you already are aware about.
[R2] On the other hand, if you are afraid that you will have to fix it, then it’s anytime better than an attack in future that might go beyond your fixing abilities.
[R3] What hackers’ want, is only at their discretion. He instead of attacking you for some confidential data may only be using your computational power to perform DOS attacks or installing bots on your corporate network etc. You never know a real hacker’s intention, until unless you experience it on your recourses.
[R4] Even a chain of house hold computers if compromised can be leveraged to bring big enterprises on their feet in the era of cyber war. Nothing is too small to matter in this world when you have computational power, access to internet, and revenue generating model.
[R5] That’s a bad approach to security! If you haven’t fixed the previous gaps identified, you might already have been victims to attacks or at worst inducing fresh vulnerabilities. The attack surface increases exponentially over a period of time, for the reason of public disclosures and exploits readily available of old/obsolete vulnerabilities. What initially required a skilled hacker to perform, if not fixed, can be exploited by a script kiddie.
[R6] Human is the weakest link in the security and irrespective of all the security guidelines and procedures you train the employees on, they are no match for an individual’s curiosity.
Clients often have a question revolving around the PenTest report categorisation. There are clients that leave the format of the report to the vendor performing PenTest or sometimes the clients supply their own template. PenTest is often regarded for providing a bulky report that clients tend to avoid paying attention to. This report can be further tweaked in different sections and sub-titles to project effective spotlight to critical items and vulnerabilities. Some of the sections that can come handy to a client are the management overview or summary where a PenTest report can have graphs, pie charts to show the observations. Then in the body section, a client should essentially see the severity ratings either on the basis of vulnerability exploitation (remote/local or ease), or exposure to its resources in reference to the findings in the network. This categorization and display of the results aids the client to understand the priority in fixing the vulnerabilities and the gaps.
All in all, a PenTest engagement is very much beneficial for the client or an enterprise, if carried out and offered with good presentations, graphs and charts. A client should consider fixing these vulnerabilities before an attacker exploits it. Moreover, these PT reports aid the client in the assessment of their network and security.
Reference: PenTest Magazine, June 2011
