Restrict Certificate Authorities (CA) to issue SSL certs. Enable CAA record in DNS

It’s been a long time since I audited someone’s DNS file but recently while checking a client’s DNS configuration I was surprised that the CAA records were set randomly “so to speak”. I discussed with the administrator and was surprised to see that he has no clue of CAA, how it works and why is it so important to enable it correctly. That made me wonder, how many of us actually know that; and how can it be a savior if someone attempts to get SSL certificate for your domain.
What is CAA?
CAA or Certificate Authority Authorization is a record that identifies which CA (certificate authorities) are allowed to issue certificate for the domain in question. It is declared via CAA type in the DNS records which is publicly viewable, and can be verified before issuing certificate by a certificate authority.
Brief Background
While the first draft was documented by Phillip Hallem-Baker and Rob Stradling back in 2010, it accelerated the work in last 5 years due to issues with CA and hacks around. The first CA subversion was in 2001 when VeriSign issued 2 certificates to an individual claiming to represent Microsoft; these were named “Microsoft Corporation”. These certificate(s) could have been used to spoof identity, and providing malicious updates etc. Further in 2011 fraudelent certificates were issued by Comodo1 and DigiNotar2 after being attacked by Iranian hackers (more on Comodo attack, and dutch DigiNotar attack); an evidence of their use in a MITM attack in Iran.
Further in 2012 Trustwave issued3a sub-root certificate that was used to sniff SSL traffic in the name of transparent traffic management. So, it’s time CA are restricted or whitelisted at domain level.
What if no CAA record is configured in DNS?
Simply put the CAA record shall be configured to announce which CA (certificate authorities) are permitted to issue a certificate for your domain. Wherein, if no CAA record is provided, any CA can issue a certificate for your domain.
CAA is a good practice to restrict your CA presence, and their power(s) to legally issue certificate for your domain. It’s like whitelisting them in your domain!
The process mandates a Certificate Authority4 (yes, it mandates now!) to query DNS for your CAA record, and the certificate can only be issued for your hostname, if either no record is available, or this CA has been “whitelisted”. The CAA record enables the rules for the parent domain, and the same are inherited by sub-domains. (unless otherwise stated in DNS records).
Certificates authorities interpret the lack of a CAA record to authorize unrestricted issuance, and the presence of a single blank issue tag to disallow all issuance.5
CAA record syntax/ format
The CAA record has the following format: <flag>``<tag>``<value> and has the following meaning,
Tag NameUsageflagThis is an integer flag with values 1-255 as defined in the RFC 68446. It is currently used to call the critical flag.7tagThis is an ASCII string (issue, issuewild, iodef) which identifies the property represented by the record policy.valueThe value of the property defined in the <tag>
The tags defined in the RFC have the following meaning and understanding with the CA records,
- issue: Explicitly authorizes a “single certificate authority” to issue any type of certificate for the domain in scope.
- issuewild: Explicitly authorizes a “single certificate authority” to issue only a wildcard certificate for the domain in scope.
- iodef: certificate authorities will report the violations accordingly if the certificate is issued, or requested that breach the CAA policy defined in the DNS records. (options: mailto:, http:// or https://)
DNS Software Support
As per excerpt from Wikipedia8: CAA records are supported by BIND (since version 9.10.1B),Knot DNS (since version 2.2.0), ldns (since version 1.6.17), NSD (as of version 4.0.1), OpenDNSSEC, PowerDNS (since version 4.0.0), Simple DNS Plus (since version 6.0), tinydns and Windows Server 2016.
Many hosted DNS providers also support CAA records, including Amazon Route 53, Cloudflare, DNS Made Easy and Google Cloud DNS.
Example: (my own website DNS)
As per the policy, I have configured that ONLY “letsencrypt.org” but due to Cloudflare Universal SSL support, the following certificate authorities get configured as well,
0 issue "comodoca.com"0 issue "digicert.com"0 issue "globalsign.com"0 issuewild "comodoca.com"0 issuewild "digicert.com"0 issuewild "globalsign.com"
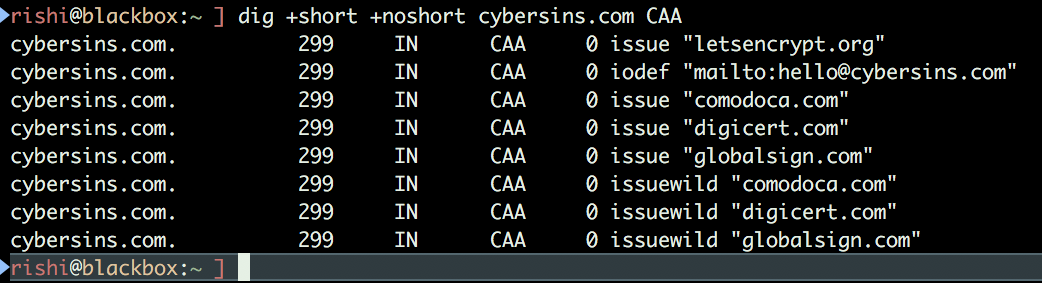
Also, configured iodef for violation: 0 iodef "mailto:[email protected]"
How’s the WWW doing with CAA?
After the auditing exercise I was curious to know how are top 10,000 alexa websites doing with CAA and strangely enough I was surprised with the results: only 4% of top 10K websites have CAA DNS record.
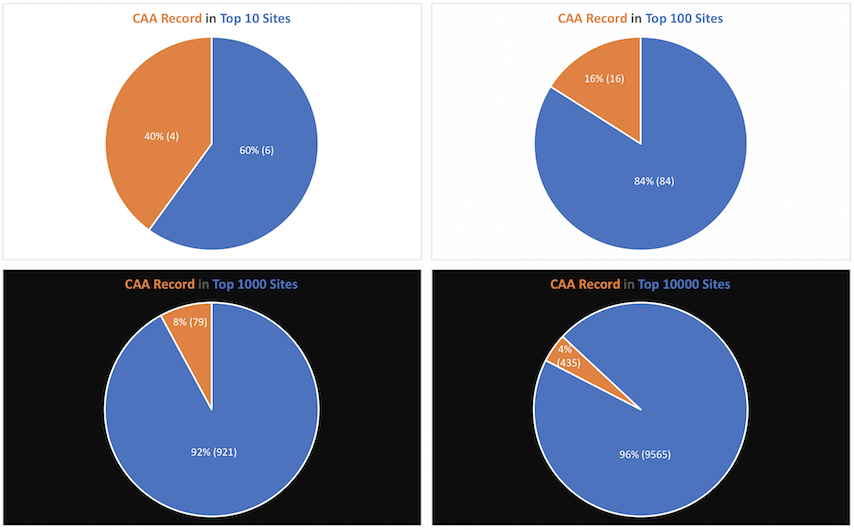
**[Update 27-Feb-18]:**This pie chart was updated with correct numbers. Thanks to Ich Bin Niche Sie for identifying the calculation error.
Now, we have still a long way to go with new security flags and policies like “CAA DNS Record”, “security.txt” file etc. and I shall be covering these topics continuously to evangelize security in all possible means without disrupting business. Remember to always work hand in hand with the business.
Stay safe, and tuned in.
Comodo CA attack by Iranian hackers: https://arstechnica.com/information-technology/2011/03/independent-iranian-hacker-claims-responsibility-for-comodo-hack/ ↩︎
Dutch DigiNotar attack by Iranian hackers: https://arstechnica.com/information-technology/2011/08/earlier-this-year-an-iranian/ ↩︎
Trustwave Subroot Certificate: http://www.h-online.com/security/news/item/Trustwave-issued-a-man-in-the-middle-certificate-1429982.html ↩︎
CAA Checking Mandatory (Ballot 187 results) 2017: https://cabforum.org/pipermail/public/2017-March/009988.html ↩︎
Wikipedia Article: https://en.wikipedia.org/wiki/DNS_Certification_Authority_Authorization ↩︎
IETF RFC 6844 on CAA record: https://tools.ietf.org/html/rfc6844 ↩︎
The confusion of critical flag: https://tools.ietf.org/html/rfc6844#section-7.3 ↩︎
Wikipedia Support Section: https://en.wikipedia.org/wiki/DNS_Certification_Authority_Authorization#Support ↩︎
